Beware these VPNs
-
I do occasionally. There are times when certain websites (Not the coffee room!) which are blocked that I would like to access.
-
@Mik said in Beware these VPNs:
I use PIA, which is aptly named. Really slows things down.
I do too, but I've not noticed any real-time slowdowns. Running SpeedTest does show a hit, of course, but it's not serious enough to be an issue in routine use.
Unless, of course, you want that German pr0n, in which case speed is of the essence, as Jon will attest.
-
My experience has been that anything over 25 is more than adequate for browsing, streaming etc. Probably anything more that 12.
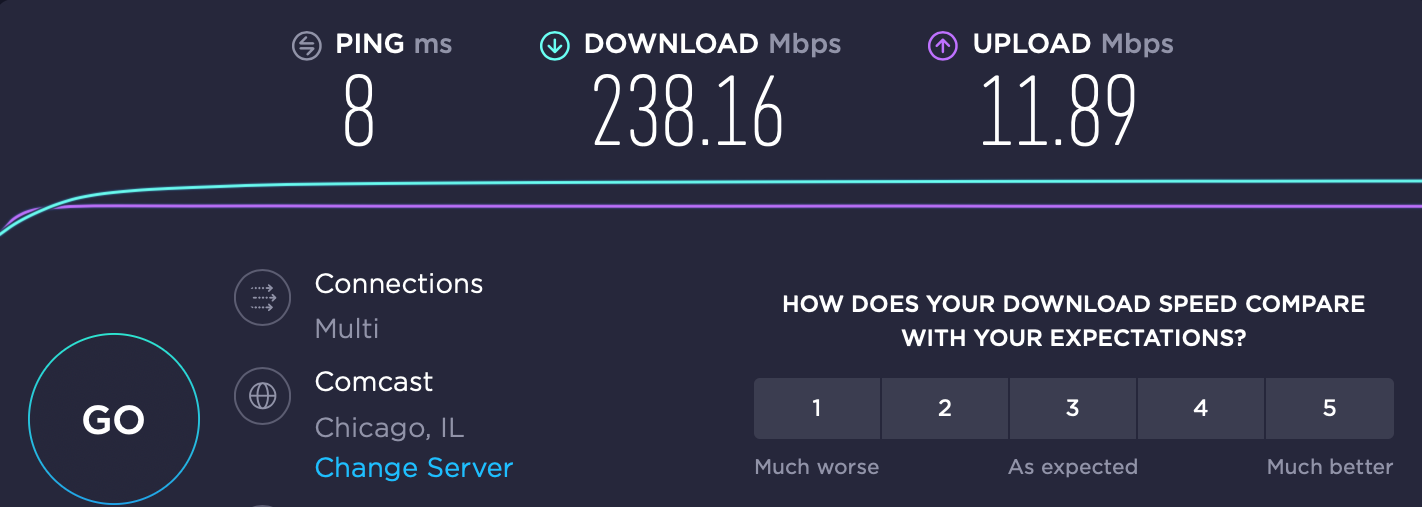
Here's what I get right now with an ethernet connection to my router for Comcast:
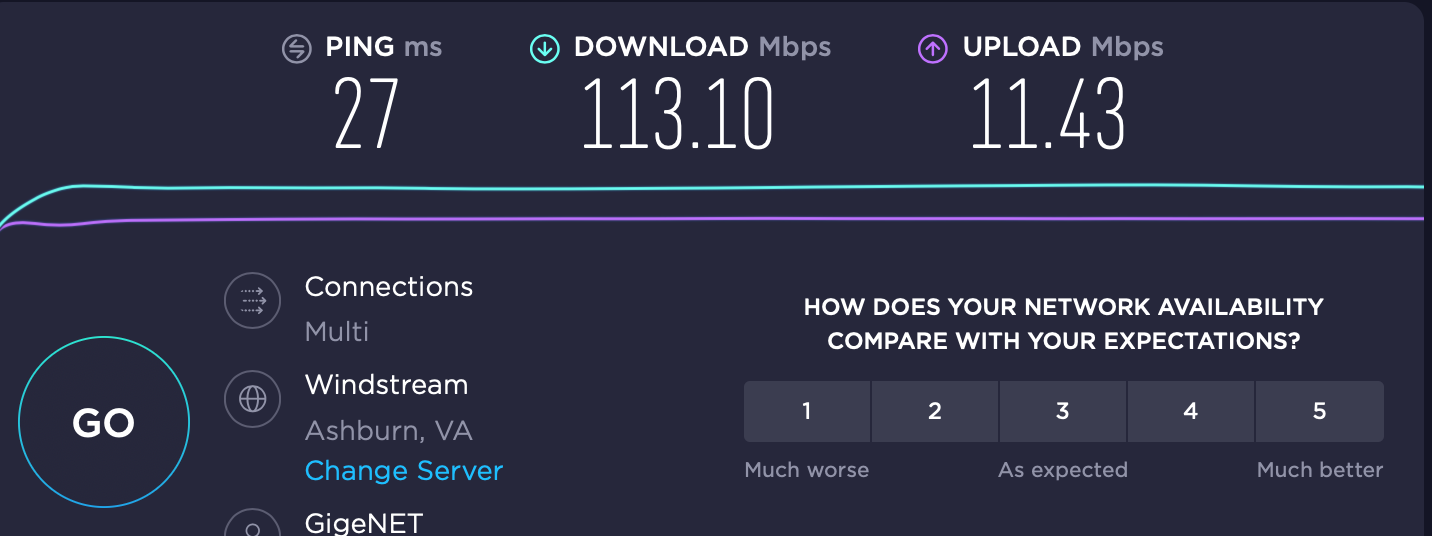
Connecting to Washington DC via PIA, I get this. About half the speed, but more than adequate:
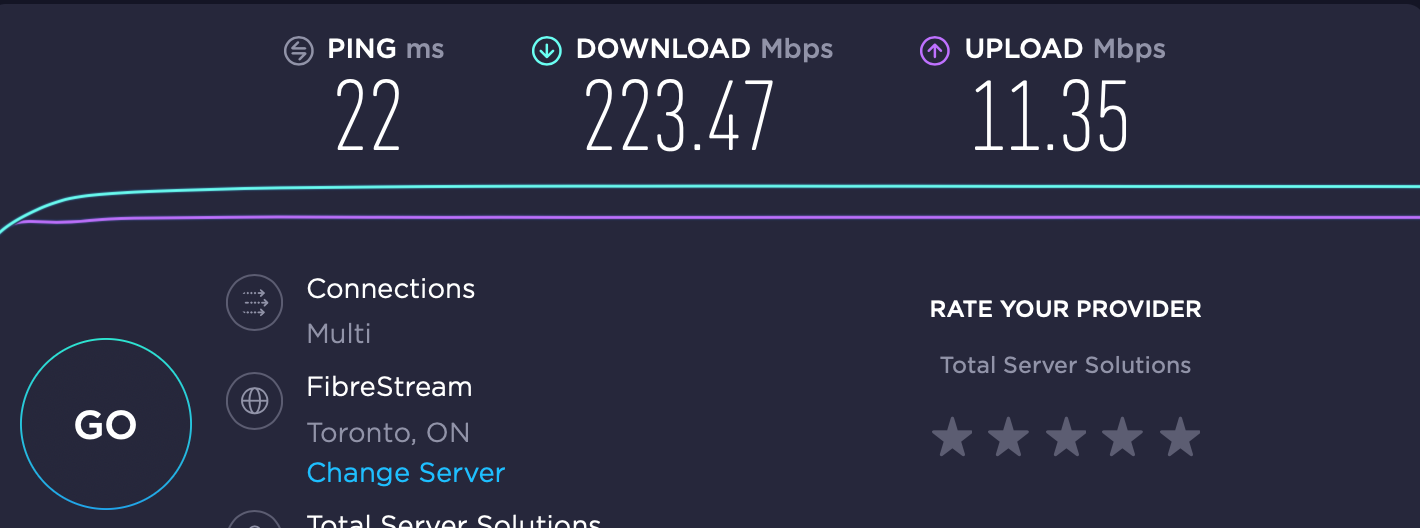
Let's go to Canada, eh?
A while ago, I saw an article, and I think I posted about it, how many people are paying for broadband they really don't need, or even use.
Does it really matter if you spend two minutes or eight minutes to download some JonPr0n? Probably not.
-
For personal use, I don't really see the need.
I do not see the need to "hide" which Internet sites I connect to. Using a commercial VPN service simply means that the VPN provider has a full record of which Internet sites I connect to.
For encryption, it's pretty much HTTPS (TLS) everywhere these days. I am comfortable enough with that to not bother with getting a VPN service.
The only caution I'd advise is this: be careful with public Wi-Fi hotspots. Most of the time you really do not know who operate these Wi-Fi hotspots and what data security and data privacy policies govern these hotspots, or if such policies exist at all. When you are not at home (where you operate the Wi-Fi network) and not at work (where your employer operates the Wi-Fi network), just use your mobile phone's cellular data to get onto the Internet, tether your laptop through your mobile phone if you need to get online with your laptop.
-
For personal use, I don't really see the need.
I do not see the need to "hide" which Internet sites I connect to. Using a commercial VPN service simply means that the VPN provider has a full record of which Internet sites I connect to.
For encryption, it's pretty much HTTPS (TLS) everywhere these days. I am comfortable enough with that to not bother with getting a VPN service.
The only caution I'd advise is this: be careful with public Wi-Fi hotspots. Most of the time you really do not know who operate these Wi-Fi hotspots and what data security and data privacy policies govern these hotspots, or if such policies exist at all. When you are not at home (where you operate the Wi-Fi network) and not at work (where your employer operates the Wi-Fi network), just use your mobile phone's cellular data to get onto the Internet, tether your laptop through your mobile phone if you need to get online with your laptop.
-
Re: cellular data cap ... short of doing an OS upgrade or MS Office upgrade, the only thing that takes a lot of bandwidth is video streaming. The typical music videos or meme videos on websites and social media platforms are usually fine. But streaming a full feature film or TV series episodes will put a big dent in the cellular data cap.
When I (used to) travel (in the pre-pandemic days), I switch to hotel Wi-Fi if I really want to stream a movie or stream TV episodes to avoid hitting my cellular data cap. Software upgrade can always wait until I get home. If I ever need to log into any service that requires better security (e.g., bank and credit card stuff), I do that only over cellular data.
Then there is email. If you use POP or IMAP, you need to know that you have property configured the security settings to encrypt not just your emails but also your login credentials. If you are not sure about that, then use POP or IMAP only over cellular data or with a VPN. If you’re using a web interface to access your email, you are generally OK if the web service uses HTTPS. Email access using mobile app (e.g., Apple Mail app, Gmail app) for well known providers (e.g., iCloud, Gmail, Yahoo! Mail) are also generally OK over hotel Wi-Fi.
-
@jon-nyc said in Beware these VPNs:
I’d pay to watch the World Cup, but nobody will let me, so I do this.
What do you use to watch that really good German pr0n?
@George-K said in Beware these VPNs:
@jon-nyc said in Beware these VPNs:
I’d pay to watch the World Cup, but nobody will let me, so I do this.
that really good German pr0n?
"Ooh ya, pull that plow, baby! Pull it! Pull it!"
-
@George-K said in Beware these VPNs:
@jon-nyc said in Beware these VPNs:
I’d pay to watch the World Cup, but nobody will let me, so I do this.
that really good German pr0n?
"Ooh ya, pull that plow, baby! Pull it! Pull it!"
@Larry said in Beware these VPNs:
@George-K said in Beware these VPNs:
@jon-nyc said in Beware these VPNs:
I’d pay to watch the World Cup, but nobody will let me, so I do this.
that really good German pr0n?
"Ooh ya, pull that plow, baby! Pull it! Pull it!"
You forgot the umlauts, heathen.
-
I should add that, whenever we go out of town, I use a VPN to connect via the hotel's WiFi.
-
Ax, do you trust the WiFi in, say, Hiltons? From what I can tell they have a contract with att to provide it everywhere.
Or Starbucks?
I regularly trust these and others but I don’t go to my bank or vanguard or whatever. I would only do that over the cell network
-
Ax, do you trust the WiFi in, say, Hiltons? From what I can tell they have a contract with att to provide it everywhere.
Or Starbucks?
I regularly trust these and others but I don’t go to my bank or vanguard or whatever. I would only do that over the cell network
-
How I see various public or semi-public Wi-Fi hotspots in North America:
-
Marriott, Hilton - won't login to financial accounts or do any software update over their Wi-Fi, but otherwise OK with using them for most things. Stayed in enough of them to be able to tell whether a particular property's Wi-Fi/Internet access system has been brought up to the usual Marriott or Hilton standard. Every once in a while I got into a property newly acquired by the chain and the Wi-Fi doesn't look or feel right (e.g., the way the network is named, the way the login process is handled), then I just treat it like I treat Wi-Fi provided by "other hotels".
-
Transportation hubs (airports, train stations, etc.) - the challenge is, when you see a Wi-Fi network name like "ATL Free Wi-Fi", how do you know that it's really operated by the "ATL" airport? If there are obvious, publicly posted signage or public announcements that collaborate that "ATL Free Wi-Fi" is indeed sanctioned by the airport, then I treat it like I treat the Marriott or Hilton Wi-Fi. Otherwise I avoid them.
-
Regulated utilities (Comcast's XfinityWiFi, the cable consortium's CableWiFi, AT&T Wi-Fi, T-Mobile Wi-Fi, etc.) - If I can access them using the HotSpot 2.0 standard, then I treat them like I treat the Marriott or Hilton Wi-Fi. Otherwise I avoid them (because I cannot verify whether a network that's named "AT&T Wi-Fi" is indeed operated by AT&T).
-
Other hotels, restaurants - won't login to any site that requires that I login, won't do any software update over them, but I otherwise don't mind using them, especially with sites that are accessed using HTTPS/TLS. This, too, is predicated on me being able to verify that the Wi-Fi network is sanctioned by the proprietor (e.g., there are posted signage or the front desk tells me that "XYZ Wi-Fi" is indeed an amenity provided by "XYZ hotel" or "XYZ restaurant"). If I cannot verify that, then I avoid the using the network.
-
-
I think some of you guys are a little hysterical.
I'm happy to use any WiFi, regardless of how "trustworthy" it looks or how encrypted it is. I also don't hesitate to do financial stuff etc. via it.
"Security by obscurity" doesn't work. Encrypting things twice or thrice doesn't increase safety. Taking a wired connection over wireless doesn't increase safety. You choose one good tool that you can trust, then you can forget about all the other mediocre tools.
For internet communication, that tool is certificates and strong encryption, as in HTTPS and SSL/TLS. There are no realistic scenarios how even a malicious attacker who completely controls the WiFi can bypass those security mechanisms.
-
For personal use, I don't really see the need.
I do not see the need to "hide" which Internet sites I connect to. Using a commercial VPN service simply means that the VPN provider has a full record of which Internet sites I connect to.
For encryption, it's pretty much HTTPS (TLS) everywhere these days. I am comfortable enough with that to not bother with getting a VPN service.
The only caution I'd advise is this: be careful with public Wi-Fi hotspots. Most of the time you really do not know who operate these Wi-Fi hotspots and what data security and data privacy policies govern these hotspots, or if such policies exist at all. When you are not at home (where you operate the Wi-Fi network) and not at work (where your employer operates the Wi-Fi network), just use your mobile phone's cellular data to get onto the Internet, tether your laptop through your mobile phone if you need to get online with your laptop.
@Axtremus said in Beware these VPNs:
When you are not at home (where you operate the Wi-Fi network) and not at work (where your employer operates the Wi-Fi network), just use your mobile phone's cellular data to get onto the Internet, tether your laptop through your mobile phone if you need to get online with your laptop.
And how would that improve security? It isn't very hard to fake an access point for cellular data ("IMSI catcher").
-
Overall, I would say that if you make sure to get a few things right:
- configure your email to use strong encryption and certificates and disable potentially dangerous attachments
- use a modern browser and an operating system with the latest security updates
- pay attention to the usage of HTTPS, the validity of certificates, and warnings about security issues from your browser
- make sure that any other non-browser-based communication that is security-relevant uses strong encryption and certificates
- don't install stuff from random internet locations.
then this will contribute 1000x more to the safety of your internet usage than using VPNs, avoiding public WiFis, etc. For instance, if you use a VPN, then the part of the connection from the VPN provider to the host you are communicating with is still unprotected. If you use a wired connection instead of wireless, this only changes the place where an attacker needs to attack but it doesn't make it inherently more difficult.
Choose the one right tool for the job instead of the combination of multiple mediocre tools.
