I guess I should check our server...
-
https://www.wired.com/story/log4j-log4shell/
That's a rather dramatic vulnerability. If you have any server directly connected to the internet, you should check whether you are affected. If you are, your server has likely already been captured and is running crypto mining software or worse.
Luckily our server software is Python-based, but I'm not entirely sure that we are safe. I'll check. In the worst case, we can restore the server from a backup.
-
Sounds like a real BFD.
I don't understand 90% of it, however.
Basically, there's a flaw in Java (is that still a thing?) that allows anyone to insert malware into a server and use it for nefarious purposes?
ETA: Apple has patched.
https://www.macworld.com/article/559108/icloud-patch-log4shell-exploit.html
-
Sounds like a real BFD.
I don't understand 90% of it, however.
Basically, there's a flaw in Java (is that still a thing?) that allows anyone to insert malware into a server and use it for nefarious purposes?
ETA: Apple has patched.
https://www.macworld.com/article/559108/icloud-patch-log4shell-exploit.html
@george-k said in I guess I should check our server...:
Basically, there's a flaw in Java (is that still a thing?) that allows anyone to insert malware into a server and use it for nefarious purposes?
In all servers which run software that uses log4J. Which is: most Java projects. And it's not just traditional servers. Could also be routers, NAS, gaming consoles, Amazon Echo-like devices, ... .
It's a field day for hackers.
-
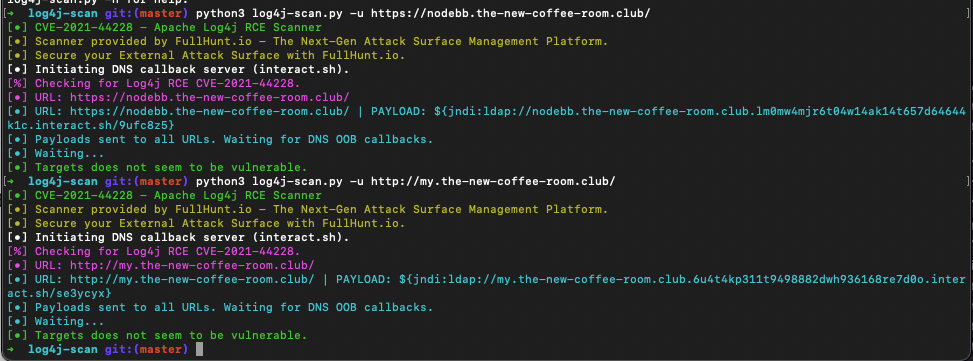
I did some checking, and so far I think our forum software as an application itself is safe from Log4Shell -- that means no random visitors or even registered/logged-in users can exploit Log4Shell just by posting/typing things into our forum software.
I have not thoroughly checked the rest of our server, so I cannot definitively tell if there may be some other software components running on our server that may be vulnerable to Log4Shell. That said, since TNCR/NodeBB is the only application we expose to the world, knowing that TNCR/NodeBB is not compromised goes a long way towards reassuring ourselves that we are OK with regards to Log4Shell.
One level down, our hosting management software Cloudron is also OK.
The only other accesses to our server would be administrative interfaces (server control panel, etc.), but that's the domain of our virtual private server provider and they should be the ones doing the testing/patching (there are limits to what I can do with these administrative interfaces).
-
Time to patch the patch.
-
This time we fixed if FOR SURE....